Fraud Detection in Finance
Overview:
Fraud is evolving and nowadays it looks more like organized crime with international and cross-functional teams involved. It means that criminals take advantage of cooperation and communication to find the weakest spots in security systems of businesses and attack them. As the world becomes more digitized, the importance of fraud detection measures also increases. Fraud prevention specialists are developing new solutions with better authentication and fraud detection.However the fraudsters are collaborating and networking on the Dark Web to learn how to break through these new technologies. So it’s critical to stay on top of the latest fraudulent tactics to prevent fraud.
Most of the Financial Institutions currently depending exclusively on rule-based systems for fraud detection which is not the most effective strategy. Fraud Detection Using Machine Learning allows Financial Institutions to run automated transaction processing in real-time. The developed ML model detects potentially fraudulent activity and flags that activity for review. This results in sharp reductions of both fraud and false positive rates at banks.
Types of Fraud:
Below are the various types of frauds:
1. Account takeover
Account Takeover happens when fraudsters acquire the login details of a legitimate user. They use the account as their own, which has terrible consequences for banks’ relationship with customers, and enables several other types of fraud and crime. It is currently one of the most widespread threats businesses face. It is almost impossible to control the way users treat their credentials. Moreover, even the most security-conscious ones can have their data stolen through a data breach, malware, phishing, social engineering attack and others. And it doesn’t matter what channel your client uses: both online and mobile are at risk.
2. Money laundering
Money laundering is a serious problem for governments all over the world. As well as impacting national security, it helps fund organized crime (drugs, terrorism, etc.), weakens economies by facilitating corruption, and increases social divisions as a result of tax evasion. For many money laundering and tax evasion scenarios, groups of organizations are victims and money is transferred between them to make detection even more difficult.
3. New account fraud and good user verification
New account fraud entails a fraudster creating an account to access goods or services under false pretenses to commit crime, steal and launder money, or gain access to services they wouldn’t be able to access using their own identity. Do I know the user trying to log in? Is this a real person or a bot? How can I make digital authentication smooth and seamless? This is where businesses are usually faced with a choice: increase security or simplify authentication steps?
Too many security steps and questions lead to an inferior customer experience and may result in the customer considering your competitor’s offering.
4. Credit Card Fraud
Credit card fraud is the most common type of payment fraud type, because digitally stored details give the criminal a much higher chance to get away with it. Also, transactions are harder to verify. Issuing banks should know when a suspicious transaction or withdrawal takes place. Spotting patterns is difficult because they have limited access to data points, only seeing the currency, amount, category, and name of the merchant.
If they try to block fraudulent payments based on these parameters, they may create high rates of false positives, which are frustrating for good cardholders. There are also legal requirements such as Strong Customer Authentication (SCA), and ensuring the source of funds is legitimate
5. Account Opening Fraud
This entails fraudsters opening new accounts by either impersonating legitimate customers or using stolen (or synthetic) identities to obtain credit.
6. Fraudulent Fund Transfers
This occurs whenever fraudsters use an emulator or app cloners to make a bank transfer or top up an account. This digital bank fraudulent scheme is often put in motion in order to launder money. Additionally, there are cases where a scammer will open a legitimate-looking account to receive deposits for promised service or product they’ll never deliver.
Challenges:
As financial and cyber criminals become ever more sophisticated in their attacks and approach to crime, the institution needs to develop new strategies to stay one step ahead. Below are some of the challenges in tackling these fraud transactions:
- Detection isn’t real-time, so fraud is detected after a financial loss occurs.
- Rules are binary and limited. They don’t accommodate the complexity and combinations of input variables that can be evaluated. This limitation results in high numbers of false positives.
- Rules are hardcoded into business logic. Curating the rules, incorporating new data sources, or adding new fraud patterns usually requires application changes that affect a business process. Propagating changes throughout a business process can be cumbersome and expensive.
- Businesses must both efficiently authenticate customers to confirm they are who they claim to be and safeguard their operations against fraud.
- Consumers who weren’t already digitally knowledgeable may find it challenging to distinguish between a legitimate engagement with an organization and a potential scam as a result of the process that comes with moving to digital.
- Consumers expect quick and easy digital journeys, but they also expect organizations to prioritize the security of their information.
- For businesses, maintaining a review of their current client risk profiles is expensive. Not just at the application stage, but throughout the customer journey.
Solutions:
Detecting fraud usually depends on correlating data from multiple sources. Most organizations aren’t set up for examining transactions across silos, so even if they can detect that fraud is taking place, they have trouble proving or blocking it.
With analytics, companies can automate the testing of 100% of data points, then identify outliers that indicate risk and investigate further. With insight into real-time, transactional data, investigators can readily see fraud as it is occurring and take immediate action to reduce the losses stemming from the fraud.
Machine Learning provides a scalable machine learning platform, where data from past fraud can be used to predict future fraud. This will even recommend a machine learning model that best fits the data and goal. Once the model is created, you can use that model to predict fraud in future transactions.
How do we achieve this?
Business Architecture:

Technical Data Architecture:
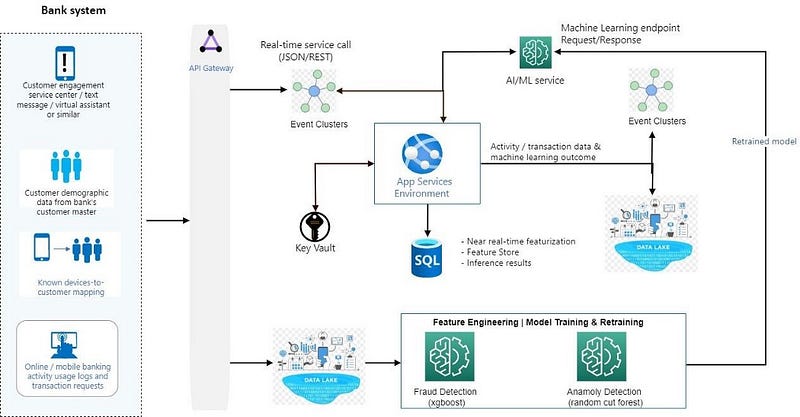
*Detailed Architecture: Enroll your interest “contact us”
There are three work streams in this architecture:
- An event-driven pipeline ingests and processes log data, creates and maintains behavioral account profiles, incorporates a fraud classification model, and produces a predictive score. Most steps in this pipeline start with an App service(Lambda/Cloud Functions). Cloud functions are used because they’re serverless, easily scaled out, and scheduled. This workload requires processing millions of incoming mobile transactions and assessing them for fraud in near real-time.
- A model training workstream combines on-premises historical fraud data and ingested log data. This workload is batch-oriented and used for model training and retraining. Orchestration processing steps includes:
- Upload of labeled historical fraud data from on-premises sources.
- Archive of data feature sets and score history for all transactions.
- Extraction of events and messages into a structured format for feature engineering and model retraining and evaluation.
- Training and retraining of a fraud model via AI/ML service.
3. The third workstream integrates with back-end business processes which helps to create a fraud management case, suspend account access, or generate a phone contact.
Benefits:
Win customer trust: online security is a top concern for most of the consumers. By successfully securing their digital experiences can win consumer trust and gain access to a wider range of data to personalize the customer relationship at every touchpoint.
Move fast and prevent losses: Move from rules to machine learning to respond in time and reduce operational costs associated with fraud
Scale flexibly: Cut through all the data complexities and implement fraud prevention at scale with the Data lake and Data Vaults.
Faster and more efficient detection: The system gets to quickly identify suspicious patterns and behaviors that might have taken human agents months to establish.
Reduced manual review time: The amount of time spent on manually reviewing information can be drastically reduced when you let machines analyze all the data points for you.
Better predictions with large datasets: A machine learning engine gets better trained the more data you feed it. Consequently, while enormous datasets can sometimes make it difficult for humans to detect patterns, this is actually the opposite with an AI-driven system.
Cost-effective solution: You only need one machine-learning system to process all the data you put at it, regardless of volume, as opposed to adding more Risk Ops agents. This is perfect for companies who see seasonal fluctuations in traffic, checkouts, or signups. A machine learning system can help your business grow without significantly raising risk management expenses concurrently.
Results:
- 45 % Reduction in Fraud investigation time
- 60% Improvement in reducing False Positives
- 50% Increase in detection of real fraud
- 25% Increase in Customer retention
Recent Post
Globally, most banks face one of the most significant issues with non-performing assets, or NPAs. For instance, the NPA ratio in India has decrea [...]
What Is a Sovereign AI Lakehouse Platform? A sovereign AI lakehouse platform unifies data lake and data warehouse capabilities with built‑in AI t [...]
Why Enterprises Are Choosing DataNature over Cloudera, Databricks, and Snowflake? Across Canada, banks, telcos, and public-sector organizations a [...]
Empowering businesses with unified data, intelligent automation, and real-time insights. Introduction: How an AI Data Platform Drives Enterprise [...]
Introduction Artificial Intelligence (AI) is quickly changing industries, and this is most obvious in the finance and banking worlds. From fraud [...]
Introduction In today’s digital environment, data-driven technologies are reshaping how companies operate. Every day, organizations produce enorm [...]
Introduction Customer data is growing at lightning speed, but making sense of it remains a challenge. This is where AI agents in customer analyti [...]
Introduction Big Data and AI are transforming the way businesses handle massive datasets. In today’s fast-paced digital world, organizations stru [...]
Introduction The Banking and Financial Services (BFSI) industry is at the edge of a major transformation. With rising customer expectations, incr [...]
Introduction In the rapidly evolving world of technology, the development of customized Large Language Models (LLMs) is a frontier being explored [...]
Introduction: In the rapidly evolving technology landscape, Data and Artificial Intelligence (AI) are reshaping industries and revolutionizing bu [...]
Introduction: Language is the glue that connects us in this digital age. From chatbots that converse with us to virtual assistants that understan [...]
In the modern business landscape, data is the new oil, powering decisions and strategies across sectors. Dlytica Inc., with its cutting-edge data [...]
Data Analyst: A Data Analyst scrutinizes numeric data to aid companies in making informed decisions. They are often the entry point for individua [...]
Introduction Collision 2023, the largest AI event of the year, served as a vibrant hub of innovation, collaboration, and knowledge-sharing. In th [...]
Overview Intelligent Document Processing (IDP) is an Artificial Intelligence (AI)-driven technology that is rapidly transforming the way business [...]
Overview In today’s fast-paced business world, companies generate a vast amount of data, most of which is stored in paper-based or unstructured d [...]
Overview The insurance industry generates a vast amount of unstructured, semi-structured and structured documents in the form of policies, claims [...]
Overview Intelligent Document Processing (IDP) refers to the use of Artificial Intelligence (AI) technologies to automate the data extraction pro [...]
In the digital age, businesses are constantly looking for ways to streamline their operations and increase efficiency. One area that holds great [...]
Overview: Intelligent Document Processing (IDP) refers to the automated process of analyzing, extracting, and categorizing data from various type [...]
Introduction: Cloud computing is a technology that allows users to store, access, and manage data and applications over the internet. Instead of [...]
Introduction to Resource Augmentation IT resource augmentation services are a growing trend in the business world, as organizations look for ways [...]
Introduction to Data Warehouse A data warehouse is a centralized repository of structured and organized data that is used for reporting, analysis [...]
Overview: Robotic process automation (RPA) is a software technology that makes it easy to build, deploy, and manage software robots that emulate [...]
How can AI automate Insurance Industry? In this article, you will learn : What is Insurance Claim Process Automation? Claims Processing is t [...]
What is CMAP? One of the premium solution provided by Dlytica is Cloud Migration Acceleration program (CMAP).Migrate to cloud with our suppo [...]
With an Innovative team at DLytica, we work on converting your Data Strategies to Solutions. We leverage a team of skilled Data Architects, Data [...]
Who are we? Company’s tagline : Drive your business with Data Analytics and AI with DLytica Inc. With an Innovative team at DLytica, we [...]
Overview: Fraud is evolving and nowadays it looks more like organized crime with international and cross-functional teams involved. It means that [...]
